Risk Assessment
Threat and risk analysis (TARA)
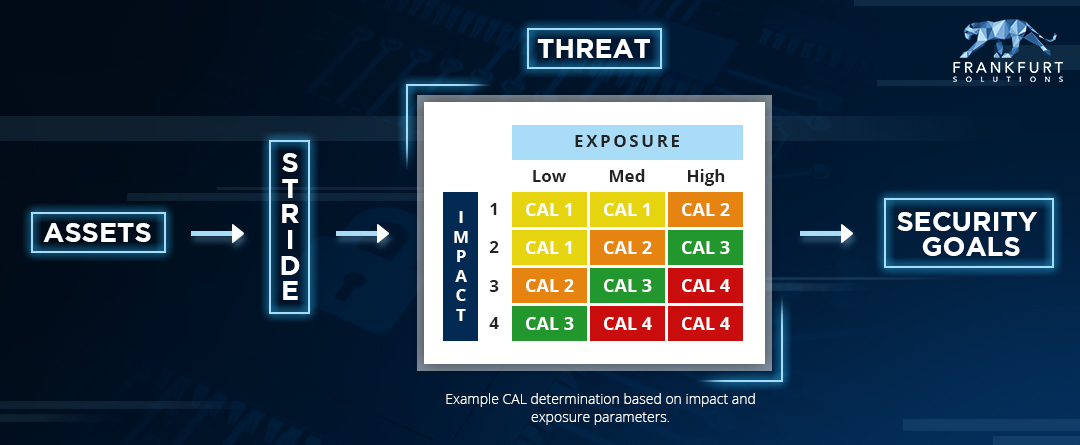
The Threat And Risk Analysis (TARA) is an attack-centric method for determining a holistic cybersecurity concept.
Based on a given architecture such an an automotive electronic control unit, technical, organizational and physical security goals and a risk classification can be determined. These serve to derive functional requirements as essential input for the design of the system, software and hardware architecture. The method can be optimally applied across different levels of abstraction and at an early stage of product design. It also provides an overview of the complex field of technical solutions and measures in the context of your product.
Content
- Classification of TARA in the secure development life cycle
- Identification of assets / system architecture
- Identification of Safety, Financial, Operational and Privacy Impact Categories
- Explanation of the valuation method
- Execution of the risk assessment with attack trees
- Derivation of safety objectives and functional requirements
- Outlook and use of the results
Results
- Holistic Product Cybersecurity Security concept
- Security by Design (avoidance of subsequent changes)
- Definition of measures beyond technical controls
- Threat classification
- Prioritisation of cybersecurity controls
- Classification of technical solutions
- Reference for penetration tests
Variants
- Threat And Risk Analysis for Connected Vehicles
- Threat And Risk Analysis for Industrial Control Systems
Duration
- 1 Day
Attendance fee
- On reqeust

